Note
Settings Management is available to Docker Business customers only.
This page contains information for admins on how to configure Settings Management to specify and lock configuration parameters to create a standardized Docker Desktop environment across the organization.
Settings Management is designed specifically for organizations who don’t give developers root access to their machines.
Prerequisites#
- Download and install Docker Desktop 4.13.0 or later.
- As an administrator, you need to enforce sign-in. This is because this feature requires a Docker Business subscription and therefore your Docker Desktop users must authenticate to your organization for this configuration to take effect. Enforcing sign-in ensures that your Docker Desktop developers always authenticate to your organization, even though they can authenticate without it and the feature will take effect. Enforcing sign-in guarantees the feature always takes effect.
Step one: Create the admin-settings.json file and save it in the correct location#
You can either use the --admin-settings installer flag on macOS or Windows to automatically create the admin-settings.json and save it in the correct location, or set it up manually.
To set it up manually:
1. Create a new, empty JSON file and name it admin-settings.json.
2. Save the admin-settings.json file on your developers' machines in the following locations:
- Mac: `/Library/Application\ Support/com.docker.docker/admin-settings.json`
- Windows: `C:\ProgramData\DockerDesktop\admin-settings.json`
- Linux: `/usr/share/docker-desktop/admin-settings.json`
By placing this file in the above protected directories, end users are unable to modify it.
> [!IMPORTANT]
>
> It is assumed that you have the ability to push the `admin-settings.json` settings file to the locations specified above through a device management software such as [Jamf](https://www.jamf.com/lp/en-gb/apple-mobile-device-management-mdm-jamf-shared/?attr=google_ads-brand-search-shared&gclid=CjwKCAjw1ICZBhAzEiwAFfvFhEXjayUAi8FHHv1JJitFPb47C_q_RCySTmF86twF1qJc_6GST-YDmhoCuJsQAvD_BwE).
Step two: Configure the settings you want to lock in#
Note
Some of the configuration parameters only apply to Windows. This is highlighted in the table below.
The admin-settings.json file requires a nested list of configuration parameters, each of which must contain the locked parameter. You can add or remove configuration parameters as per your requirements.
If locked: true, users aren't able to edit this setting from Docker Desktop or the CLI.
If locked: false, it's similar to setting a factory default in that:
- For new installs, locked: false pre-populates the relevant settings in the Docker Desktop UI, but users are able to modify it.
- If Docker Desktop is already installed and being used,
locked: falseis ignored. This is because existing users of Docker Desktop may have already updated a setting, which in turn will have been written to the relevant config file, for example thesettings.jsonordaemon.json. In these instances, the user's preferences are respected and we don't alter these values. These can be controlled by the admin by settinglocked: true.
The following admin-settings.json code and table provides an example of the required syntax and descriptions for parameters and values:
{
"configurationFileVersion": 2,
"exposeDockerAPIOnTCP2375": {
"locked": true,
"value": false
},
"proxy": {
"locked": true,
"mode": "system",
"http": "",
"https": "",
"exclude": [],
"windowsDockerdPort": 65000,
"enableKerberosNtlm": false
},
"containersProxy": {
"locked": true,
"mode": "manual",
"http": "",
"https": "",
"exclude": [],
"pac":"",
"transparentPorts": ""
},
"enhancedContainerIsolation": {
"locked": true,
"value": true,
"dockerSocketMount": {
"imageList": {
"images": [
"docker.io/localstack/localstack:*",
"docker.io/testcontainers/ryuk:*"
]
},
"commandList": {
"type": "deny",
"commands": ["push"]
}
}
},
"linuxVM": {
"wslEngineEnabled": {
"locked": false,
"value": false
},
"dockerDaemonOptions": {
"locked": false,
"value":"{\"debug\": false}"
},
"vpnkitCIDR": {
"locked": false,
"value":"192.168.65.0/24"
}
},
"kubernetes": {
"locked": false,
"enabled": false,
"showSystemContainers": false,
"imagesRepository": ""
},
"windowsContainers": {
"dockerDaemonOptions": {
"locked": false,
"value":"{\"debug\": false}"
}
},
"disableUpdate": {
"locked": false,
"value": false
},
"analyticsEnabled": {
"locked": false,
"value": true
},
"extensionsEnabled": {
"locked": true,
"value": false
},
"scout": {
"locked": false,
"sbomIndexing": true,
"useBackgroundIndexing": true
},
"allowExperimentalFeatures": {
"locked": false,
"value": false
},
"allowBetaFeatures": {
"locked": false,
"value": false
},
"blockDockerLoad": {
"locked": false,
"value": true
},
"filesharingAllowedDirectories": [
{
"path": "$HOME",
"sharedByDefault": true
},
{
"path":"$TMP",
"sharedByDefault": false
}
],
"useVirtualizationFrameworkVirtioFS": {
"locked": true,
"value": true
},
"useVirtualizationFrameworkRosetta": {
"locked": true,
"value": true
},
"useGrpcfuse": {
"locked": true,
"value": true
},
"displayedOnboarding": {
"locked": true,
"value": true
}
}
| Parameter | Description | |
|---|---|---|
configurationFileVersion |
Specifies the version of the configuration file format. | |
exposeDockerAPIOnTCP2375 |
Windows only | Exposes the Docker API on a specified port. If value is set to true, the Docker API is exposed on port 2375. Note: This is unauthenticated and should only be enabled if protected by suitable firewall rules. |
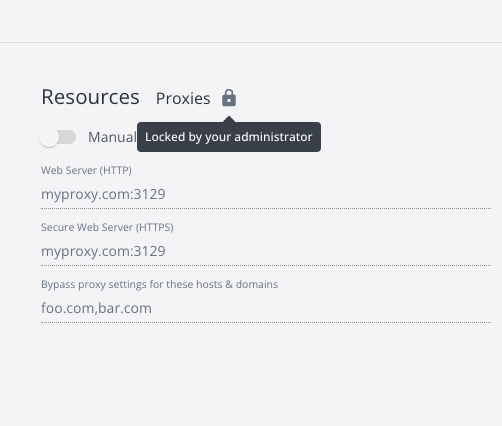
proxy |
If mode is set to system instead of manual, Docker Desktop gets the proxy values from the system and ignores and values set for http, https and exclude. Change mode to manual to manually configure proxy servers. If the proxy port is custom, specify it in the http or https property, for example "https": "http://myotherproxy.com:4321". The exclude property specifies a comma-separated list of hosts and domains to bypass the proxy. |
|
windowsDockerdPort |
Windows only | Exposes Docker Desktop's internal proxy locally on this port for the Windows Docker daemon to connect to. If it is set to 0, a random free port is chosen. If the value is greater than 0, use that exact value for the port. The default value is -1 which disables the option. Note: This is available for Windows containers only. |
enableKerberosNtlm |
When set to true, Kerberos and NTLM authentication is enabled. Default is false. Available in Docker Desktop version 4.32 and later. For more information, see the settings documentation. |
|
containersProxy (Beta) |
Allows you to create air-gapped containers. For more information see Air-Gapped Containers. | |
enhancedContainerIsolation |
If value is set to true, Docker Desktop runs all containers as unprivileged, via the Linux user-namespace, prevents them from modifying sensitive configurations inside the Docker Desktop VM, and uses other advanced techniques to isolate them. For more information, see Enhanced Container Isolation. |
|
dockerSocketMount |
By default, enhanced container isolation blocks bind-mounting the Docker Engine socket into containers (e.g., docker run -v /var/run/docker.sock:/var/run/docker.sock ...). This allows admins to relax this in a controlled way. See ECI Configuration for more info. |
|
imageList |
Indicates which container images are allowed to bind-mount the Docker Engine socket. | |
commandList |
Restricts the commands that containers can issue via the bind-mounted Docker Engine socket. | |
linuxVM |
Parameters and settings related to Linux VM options - grouped together here for convenience. | |
wslEngineEnabled |
Windows only | If value is set to true, Docker Desktop uses the WSL 2 based engine. This overrides anything that may have been set at installation using the --backend=<backend name> flag. |
dockerDaemonOptions |
If value is set to true, it overrides the options in the Docker Engine config file. See the Docker Engine reference. Note that for added security, a few of the config attributes may be overridden when Enhanced Container Isolation is enabled. |
|
vpnkitCIDR |
Overrides the network range used for vpnkit DHCP/DNS for *.docker.internal |
|
kubernetes |
If enabled is set to true, a Kubernetes single-node cluster is started when Docker Desktop starts. If showSystemContainers is set to true, Kubernetes containers are displayed in the UI and when you run docker ps. imagesRepository allows you to specify which repository Docker Desktop pulls the Kubernetes images from. For example, "imagesRepository": "registry-1.docker.io/docker". |
|
windowsContainers |
Parameters and settings related to windowsContainers options - grouped together here for convenience. |
|
dockerDaemonOptions |
Overrides the options in the Linux daemon config file. See the Docker Engine reference. | |
disableUpdate |
If value is set to true, checking for and notifications about Docker Desktop updates is disabled. |
|
analyticsEnabled |
If value is set to false, Docker Desktop doesn't send usage statistics to Docker. |
|
extensionsEnabled |
If value is set to false, Docker extensions are disabled. |
|
scout |
Setting useBackgroundIndexing to false disables automatic indexing of images loaded to the image store. Setting sbomIndexing to false prevents users from being able to index image by inspecting them in Docker Desktop or using docker scout CLI commands. |
|
allowExperimentalFeatures |
If value is set to false, experimental features are disabled. |
|
allowBetaFeatures |
If value is set to false, beta features are disabled. |
|
blockDockerLoad |
If value is set to true, users are no longer able to run docker load and receive an error if they try to. |
|
filesharingAllowedDirectories |
Specify which paths your developers can add file shares to. Also accepts $HOME, $TMP, or $TEMP as path variables. When a path is added, its subdirectories are allowed. If sharedByDefault is set to true, that path will be added upon factory reset or when Docker Desktop first starts. |
|
useVirtualizationFrameworkVirtioFS |
macOS only | If value is set to true, VirtioFS is set as the file sharing mechanism. Note: If both useVirtualizationFrameworkVirtioFS and useGrpcfuse have value set to true, VirtioFS takes precedence. Likewise, if both useVirtualizationFrameworkVirtioFS and useGrpcfuse have value set to false, osxfs is set as the file sharing mechanism. |
useVirtualizationFrameworkRosetta |
macOS only | If value is set to true, Docker Desktop turns on Rosetta to accelerate x86_64/amd64 binary emulation on Apple Silicon. Note: This also automatically enables Use Virtualization framework. |
useGrpcfuse |
macOS only | If value is set to true, gRPC Fuse is set as the file sharing mechanism. |
displayedOnboarding |
If value is set to true, the onboarding survey will not be displayed to new users. Setting value to false has no effect. |
Step three: Re-launch Docker Desktop#
Note
Administrators should test the changes made through the
admin-settings.jsonfile locally to see if the settings work as expected.
For settings to take effect: - On a new install, developers need to launch Docker Desktop and authenticate to their organization. - On an existing install, developers need to quit Docker Desktop through the Docker menu, and then relaunch Docker Desktop. If they are already signed in, they don't need to sign in again for the changes to take effect.
Important
Selecting Restart from the Docker menu isn't enough as it only restarts some components of Docker Desktop.
Docker doesn't automatically mandate that developers re-launch and sign in once a change has been made so as not to disrupt your developers' workflow.
In Docker Desktop, developers see the relevant settings grayed out and the message Locked by your administrator.